This blog post and associated script assume that you have the ability to Manage DLP for your Slack / your organizations Slack.
Slack’s native data export functionality, even on Enterprise Grid plans, is not a perfect solution. While it can provide access to messages and files, the format and process present significant challenges. For audit logs, data can be exported as raw JSON or CSV files through the UI:
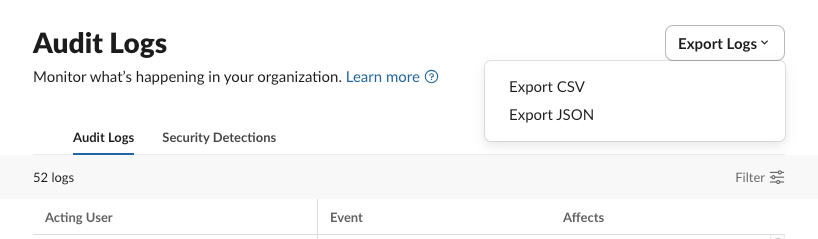 Export Functionality for Slack Audit Logs
Export Functionality for Slack Audit Logs
However, Slack’s Data Loss Prevention (DLP) solution lacks the same functionality:
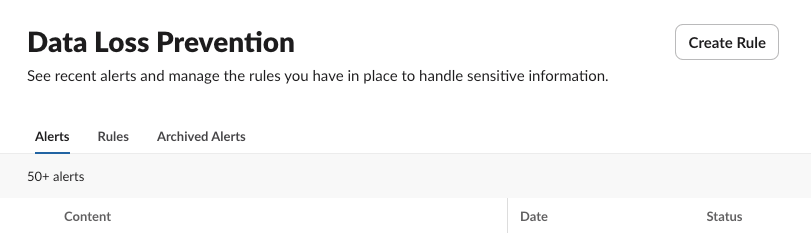 Export Functionality for Slack Audit Logs
Export Functionality for Slack Audit Logs
Even clicking through the individual events only provide you with options to either archive the alert or delete the message. This means that if you want to copy the data, you either need to go through the manual effort of copying everything into the format you require or using expensive third-party tools to reassemble the data for review.
Exporting the Data through Python
If it’s not exportable through the UI, there has to be an easier way to retrieve the content than copying the items manually. Diving into the networks tab, we can see a call to the https://<DOMAIN>/api/admin.dlp.violations.list endpoint:
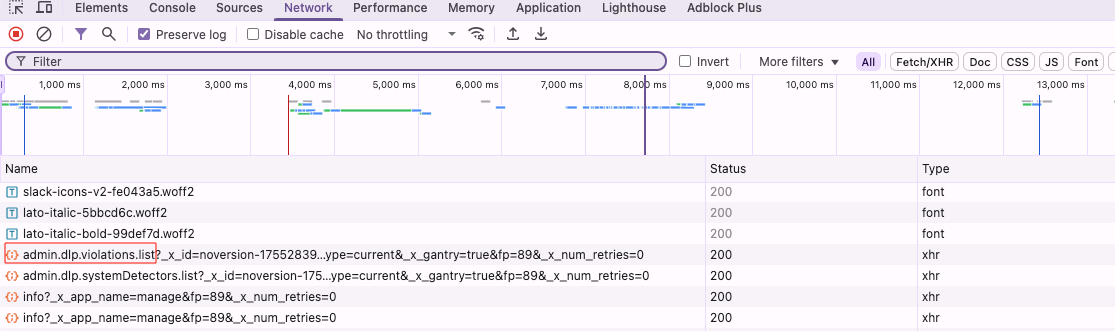 Network Connections for Slack’s DLP Admin Page
Network Connections for Slack’s DLP Admin Page
After messing around with some Python requests, I created a simple script to export the data in JSON format. The script itself is rather simple but it uses two specific tokens - a Slack Token and a Slack Cookie:
- SLACK_XOXC_TOKEN: This is a personal user session token generated by the Slack web or desktop app, it can be found in a requests payload.
- SLACK_XOXD_TOKEN: This is the session cookie which can be found in the browser’s cookie storage.
According to Slack, these tokens are used by the web client, are cookie-dependent and, while functional, are not supported or recommended for official API integrations. Slack recommends using standard tokens like bot (xoxb-) or user (xoxp-) tokens instead.
When paired (xoxc- from local storage and xoxd- from the cookie) they grant full user-level API access without requiring OAuth or bot setup. This blog post by PaperMtn describes how to retrieve the cookie from the console. It also describes methods that can be used to convert the session cookie (d) into a token, if required.
Once the script has run, you can use the following JQ commands to export the JSON data into CSV format:
Retrieve Specific Data using JQ
1
2
3
4
5
6
7
cat dlp-output.json | jq '.violation_alerts[] | {
"dlp_rules": [.rules[].name],
"name": .conversations[].name,
"is_private": .conversations[].is_private,
"created": .date_create | todateiso8601,
"text": .summary
}' > condensed_output.json
Export the Required JSON Data to a CSV file
1
2
3
4
5
6
7
8
cat condensed_output.json | jq -r '
[
.created,
.is_private,
.name,
(.dlp_rules | join("|")),
.text
] | @csv' > output.csv
I hope you found this post useful for extracting data from Slack DLP. As always, if you have any questions or comments, please reach out!
